Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
Broadcom Delivers Industry-leading Network Monitoring Scale to Meet the Demands of the Pandemic
How to Do Simple UX Monitoring With ipMonitor
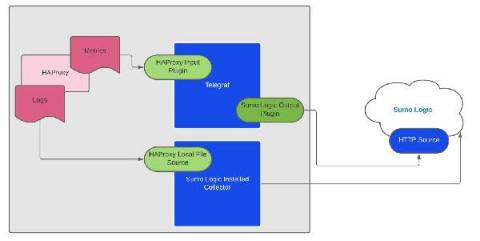
Testing Your HAProxy Configuration
Learn how to test your HAProxy Configuration. Properly testing your HAProxy configuration file is a simple, yet crucial part of administering your load balancer. Remembering to run one simple command after making a change to your configuration file can save you from unintentionally stopping your load balancer and bringing down your services.
Calico integration with WireGuard using kOps
It has been a while since I have been excited to write about encrypted tunnels. It might be the sheer pain of troubleshooting old technologies, or countless hours of falling down the rabbit hole of a project’s source code, that always motivated me to pursue a better alternative (without much luck). However, I believe luck is finally on my side.
Firewall... It's getting hot in here!
There’s something that humans and machines have in common, and no, it’s not the disappointment suffered by the final season of Game of Thrones, or, well, at least not only that. What we have in common is that we need protection. You know, animals need it too, and plants, but if you’ve gotten this far, it seems that you’re interested in computers, networks and all these pretty modern “geek” things, so today we’ll talk about that kind of protection.
What's in a Name? "Network Specialist" vs. "Network Engineer"
Why you should be using a VPN when working from home
With so many of us working from home full time for the last 16 months, VPNs have become essential tools for companies to keep their staff working in a safe environment. What we mean by “safe” is mainly about your online presence whilst performing daily tasks for your job.
Improving Web Page Load Time
HTTP/2 (originally named HTTP/2.0) was a major revision of the HTTP network protocol used by the World Wide Web published in 2015. Indeed, those in the Citrix/EUC ecosystem may remember Marius Sandbu investigating the benefits of HTTP/2 for NetScaler, Microsoft IIS, and Storefront users back in 2015/6. HTTP/2 was the first new version of HTTP since HTTP/1.1, which itself was standardized in RFC 2068 in 1997.