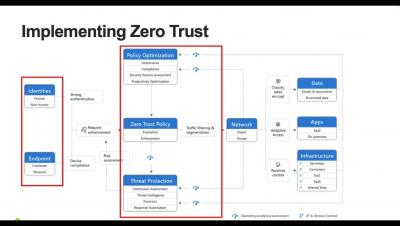
Endpoint Monitoring Explained with Example
Today, people and businesses use endpoints to accomplish everything from day-to-day tasks to large projects. Endpoints include the physical devices that connect to and communicate with a central network. They are used to manipulate data or exchange information. The number of endpoint devices that average businesses and enterprises manage is 135,000, and that number continues to grow.