Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
CFEngine 3.15.7 and 3.18.3 released
We are pleased to announce two new patch releases for CFEngine, version 3.15.7 and 3.18.3! These releases mainly contain bug fixes and dependency updates.
5 Important Operations Issues to Consider When Working With an International Team
Jason Chan on Harnessing Security Automation to Manage Cyberthreat Complexity
Jason Chan on How Automation Transformed Netflix's Cybersecurity Posture
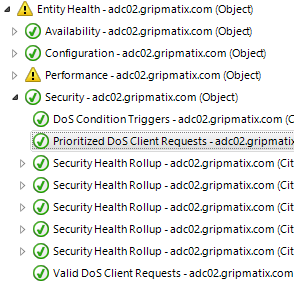
Citrix NetScaler Denial-of-Service (DoS) JavaScript Triggers
Are you aware when Denial-of-Service (DoS) JavaScript triggers occur on your Citrix NetScaler devices to block DoS attacks? Do you know when exceptions are made based on 'valid' DoS cookies? MetrixInsight for NetScaler monitors for these occurrences and alarms you whenever this happens (too often).
Effective vulnerability management for your microservices
Do VPNs Really Keep Your Browsing Data Private?
Cloud Security: Indiana Bob's Server Closet Versus Data Centers | Security Insights Podcast, Episode 28
Amanda and Chris share stories proving why your data really is more secure in the cloud than the average on-premises server closet – and what organizations should worry more about when it comes to data security.
Secure Backup Strategies for 2022
Hard drive crash. Ransomware. Equipment failure. Accidental deletion. Theft. There are plenty of reasons why end users want to have a secure and up-to-date backup of their most important files. And there are just as many approaches to backup and recovery as there are reasons to want it in place. In this article, we’ll discuss practical strategies and best practices for backing up important data, including consumer-level options and how to get the most from an enterprise-grade backup solution.