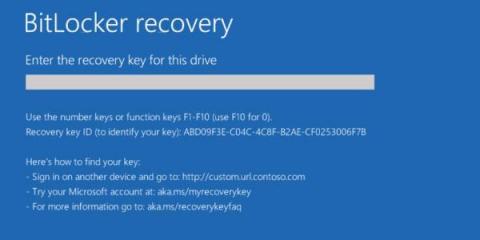
3-Step Approach to Eliminate the BitLocker Recovery Key Backup Issue using Nexthink
In today’s era of “Work from anywhere”, Data Security & Data Encryption has become a vital security step for organisations world-wide and a key component for security compliance. BitLocker is one of the popular Software Stacks for enforcing encryption on all devices & drives. Exponential complexity for managing the encryption compliance and the backup of the recovery keys for all devices in the organization has increasingly become a key challenge for EUC Professionals.