Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Demo Den: Open DevOps, Security in Jira (Feb 2023)
Integrate CircleCI with HashiCorp Vault using OIDC
Well-designed secrets management is a delicate balancing act between security and usability. Secrets must be easily accessible to the right users when building and deploying, but they must also at the same time be well-secured and easy to rotate. This article will cover how to thread this needle by integrating CircleCI with HashiCorp Vault and retrieving secrets using short-lived OpenID Connect (OIDC) authentication tokens.
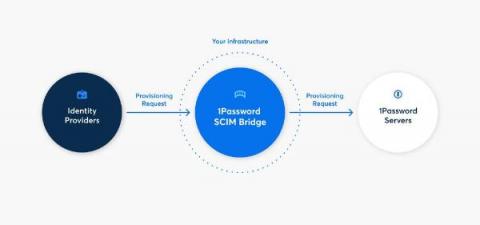
How 1Password Relies on Checkly for Secure System Health Monitoring for Thousands of Business Customers
1Password uses Checkly to provide transparent, advanced synthetic monitoring to 1Password SCIM bridge customers 1Password is a leader in human-centric security and privacy, with a solution that’s built from the ground up to enable anyone—no matter the level of technical proficiency—to navigate the digital world without fear or friction when logging in.
Be ransomware ready with cloud-first DPaaS
Did you know that your choice of a data protection solution can not only help you recover from cyber-attacks, but can also reduce your vulnerability to those attacks? By storing your primary backups safely off the local network, and choosing a remotely hosted SaaS data protection application, two critical attack vectors will be safely out of the reach of ransomware.
Webinar Recap: How Observability Impacts SRE, Development, and Security Teams
In today’s fast paced and constantly evolving digital landscape, observability has become a critical component of effective software development. Companies are relying more on and using machine and telemetry data to fix customer problems, refine software and applications, and enhance security. However, while more data has empowered teams with more insights, the value derived from that data isn’t keeping pace with this growth. So how can these teams derive more value from telemetry data?
LIVE NOW: State of DevOps | A Look Ahead at 2023
Kubernetes network monitoring: What is it, and why do you need it?
In this article, we will dive into Kubernetes network monitoring and metrics, examining these concepts in detail and exploring how metrics in an application can be transformed into tangible, human-readable reports. The article will also include a step-by-step tutorial on how to enable Calico’s integration with Prometheus, a free and open-source CNCF project created for monitoring the cloud.
Endpoint Security Explained
Black Kite reported that 53% of organizations were hit by ransomware attacks in 2021, and that number was expected to increase to 69% in 2022. Cyberattacks show no sign of slowing, so it is critical that organizations have necessary cybersecurity precautions in place. One of the best ways to protect your IT environment is with an endpoint security process.
Deciphering container complexity from operations to security
Kubernetes turns 9 this year and with its maturity each year, it brings new challenges that drive seismic influence across the rapidly changing cloud native ecosystem. Each year we see new tools created and existing solutions optimized from new lightweight distributions, new features across Kubernetes management platforms, and container security solutions, all adding value to users but simultaneously contributing to the complexity are facing to run Kubernetes successfully.