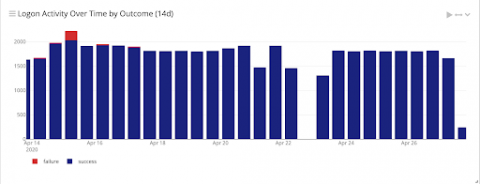
How Calico Cloud's runtime defense mitigates Kubernetes MITM vulnerability CVE-2020-8554
Since the release of CVE-2020-8554 on GitHub this past December, the vulnerability has received widespread attention from industry media and the cloud security community. This man-in-the-middle (MITM) vulnerability affects Kubernetes pods and underlying hosts, and all Kubernetes versions—including future releases—are vulnerable. Despite this, there is currently no patch for the issue.