Onelogin Log Insights with Coralogix
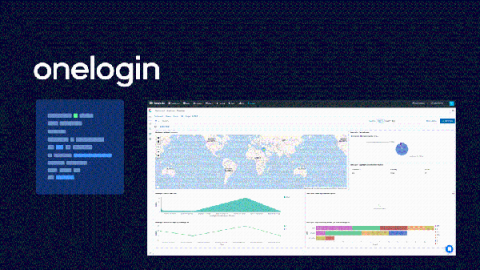
OneLogin is one of the top leading Unified Access Management platforms, enabling organizations to manage and Access their cloud applications in a secure way. OneLogin makes it simpler and safer for organizations to access the apps and data they need anytime, everywhere. This post will show you how Coralogix can provide analytics and insights for your OneLogin log data – including performance and security insights.