Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
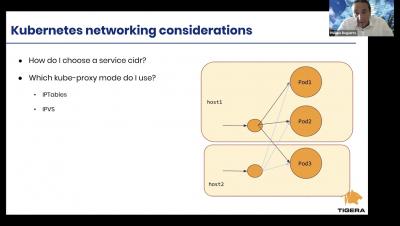
Getting up and running with Calico Enterprise on your Rancher K8s Cluster
Introduction to security monitoring
Security Information Monitoring or Security Event Monitoring is part of Security Information Management. Yes, I acknowledge they are flashy names and that even experts have their differences about concept and scope. Here in Pandora FMS, flexibility is part of our name, so, hereby, I will abbreviate it as Security Monitoring. As you can see, it is short and manageable!
Enabling DevSecOps with the Elastic Stack
Software development and delivery is an ever-changing landscape. Writing software was once an art form all its own, where you could write and deploy machine code with singleness of purpose and no concern for things like connecting to other computers. But as the world and the variety of systems that software supports became more complex, so did the ecosystem supporting software development.
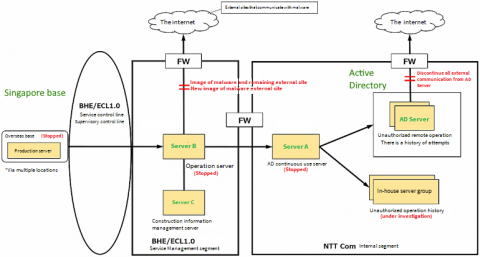
Telecommunications giant reveals an Active Directory server breach. What can we learn from it?
We’ve always been vocal about the imminent threat of breaches and propagated the message that irrespective of the size of your business, the industry you’re in, or your geography, you can be subject to a security breach. And unfortunately, history repeats itself often. On May 11, 2020, Nippon Telegraph & Telephone (NTT), a large telecommunications company, revealed that attackers may have stolen data from its internal systems, affecting over 600 customers.
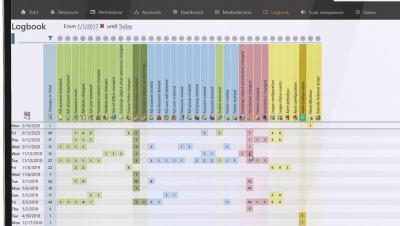
SolarWinds Access Rights Manager Overview
Kubernetes Secrets - The good the bad and the ugly
Secrets, by definition, should be kept secret, whichever tool you’re using. While there are plenty of best practices for keeping your Kubernetes secrets actually secret, there are some loopholes that can compromise their security, and might be taken advantage of by malicious entities. This post will cover prevalent best practices for securing your secrets on Kubernetes along with some new approaches for secrets management.
Personal Information Security and OnPage's Commitment to User Privacy
When making purchasing decisions, organizations must consider a vendor’s product pricing, promised benefits and level of customer service. Thorough vendor evaluation tends to result in successful investments, allowing organizations to reap the benefits of their newly acquired products without buyer’s remorse. Unfortunately, some buyers dismiss the importance of personal information security and how the vendor promises to protect user data.
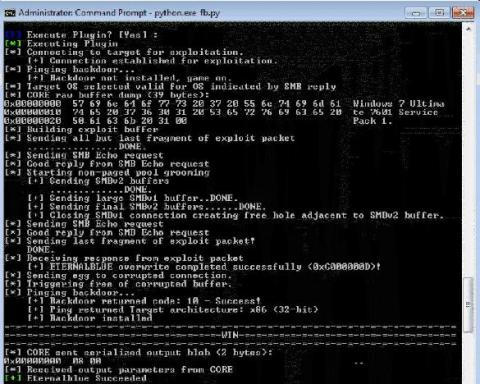
Defense in depth: DoublePulsar
Leverage advanced analytics to secure your endpoint devices
With the new normal adding several more challenges and variables to the security layer, how do you ensure your data is safeguarded without increasing the workload or the headcount of your security team? Using advanced analytics, in tandem with endpoint monitoring applications such as ManageEngine’s Mobile Device Manager Plus and Desktop Central, will help you better visualize and analyze your endpoint data, identify patterns, and establish correlations.