KEDB Explained: Key Insights and Benefits for IT Service Management
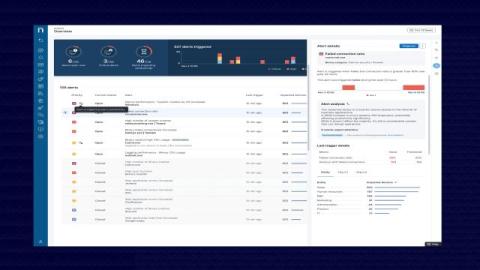
Rather than striving for immediate perfection, which can be unrealistic in complex IT environments, the KEDB, or Known Error Database, provides a practical approach. Teams use KEDBs to document known errors and their workarounds so they can address issues efficiently and keep systems running while more permanent solutions are developed. It's an approach that not only keeps operations on track but also supports ongoing improvements and knowledge sharing within the organization.