What's new in Sysdig - March 2021
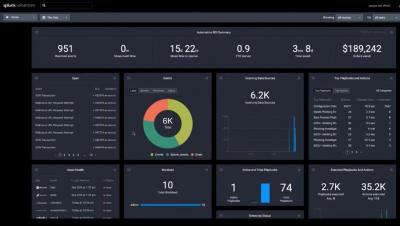
Welcome to another monthly update on what’s new from Sysdig. Our team continues to work hard to bring great new features to all of our customers, automatically and for free! This month was mostly about compliance and a PromQL Query Explorer! Have a look below for the details. We have added a number of new compliance standards to our compliance dashboards page, making it even easier for our customers to quickly (and continuously!) check how well they’d do from an audit.