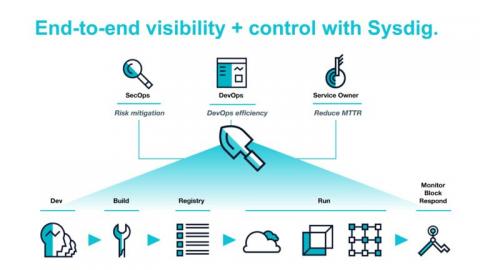
Understanding RBAC in Sensu Go
Regulating access to resources is a fundamental measure for enterprises to ensure the security and reliability of a system. The last thing you need is a stolen or weak password to give up the keys to the proverbial kingdom. With role-based access control (RBAC), this risk is mitigated by providing only the necessary access so a user in your organization doesn't have more access than needed.