Operations | Monitoring | ITSM | DevOps | Cloud
Alerting
Synthetic monitoring as Code with Checkly and ilert
This post will introduce Checkly, the synthetic monitoring solution, and their monitoring as code approach. This guest post was written by Hannes Lenke, the CEO, and co-founder of Checkly. First, thanks to Birol and the ilert team for the opportunity to introduce Checkly. ilert recently announced discontinuing its uptime monitoring feature and worked with us on an integration to ensure that existing customers could migrate seamlessly. So, what is monitoring as code and Checkly?
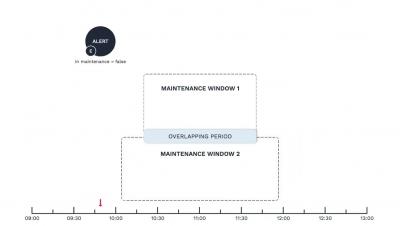
Overlapping Maintenance Windows in Moogsoft Cloud | Moogsoft Product Videos & How-Tos
IT Incident Management - What is it and how to do it?
Are you tired of dealing with IT incidents that seem to pop up at the worst possible times? Do you find yourself struggling to keep track of all the moving pieces involved in resolving incidents? If so, it’s time to revitalize your incident management strategy. In this article, we’ll explore the key pillars of incident process management, best practices, and how technology can help streamline your process.
What makes AlertOps the top choice as an Opsgenie alternative
Alert Tuning Recommendations: Reinventing Anomaly Alerts with Anodot
In the complex and dynamic realm of data analytics, real-time anomalies serve as insights to issues a business faces. A pervasive and enduring conundrum persists: accurately discerning between anomalies of significant importance and those of lesser consequence. This distinction is a nontrivial task as not all anomalies bear the same weight.
Receiving MySQL database Alerts
Imagine your popular website or app suddenly slowing down significantly or even stopping altogether. You scramble to find the root cause while losing customers and income every minute. This stressful situation is all too familiar, but you can avoid it. Proactively monitoring MySQL databases can help prevent these issues and keep your performance at its best.
Performance Ratings and Experience Scores for Meaningful Alerting and Rapid Observability
Administrators and IT management are increasingly leveraging simple quantifiable KPI indicators such as “Performance Ratings” to gain rapid overviews and track key outcomes. Modern IT architectures are designed and built to scale and be resilient. Systems are now usually built to handle failover and auto-scale up and down to handle varying demand and workloads with very different properties and needs.