Elastic 7.9 released, with free distribution tier of features of Workplace Search and endpoint security
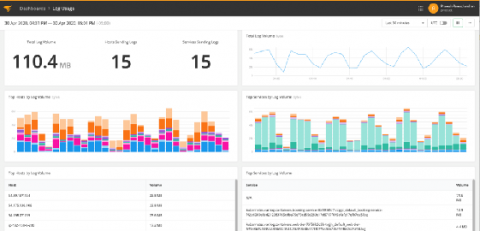
We are pleased to announce the general availability of Elastic 7.9. This release brings a broad set of new capabilities to our Elastic Enterprise Search, Observability, and Security solutions, which are built on the Elastic Stack — Elasticsearch, Kibana, Logstash, and Beats.