Operations | Monitoring | ITSM | DevOps | Cloud
Monitoring
The latest News and Information on Monitoring for Websites, Applications, APIs, Infrastructure, and other technologies.
Evolve hybrid cloud security to meet COVID-19 challenges
Remote work poses new demands for hybrid cloud security. Here’s how organizations can protect themselves from security threats in this complex landscape.With employees continuing to work from home to meet the social distancing requirements of COVID-19, more people are juggling business with personal engagements, at times outside normal business hours. Often, they’re using their mobile business laptop, as well as a plethora of additional wireless mobile devices.
Salesforce Application Performance Monitoring
Can you imagine trying to keep track of all your prospect- and customer-related activities on a spreadsheet? What about ye olde days of rolodexes (do people still remember what those are?!)? Thank goodness for Salesforce, the Customer Relationship Management (CRM) solution that revolutionized sales, marketing, and customer care - and how we interact with customers in general. Salesforce is a critical component for many businesses.
Planning Ahead to Maximize the Value of Attending VMworld
The difference between attending as magnificent an event as VMworld with, versus without, a plan of attack is a night versus day experience. I’ve had the good fortune of attending this event as both a speaker and an attendee, and I look back with fondness on the interactions and experience. However, both those visits were in person. As I prepared to attend VMworld virtually for the first time, I wondered if my plan of attack would change? Turned out, not so much.
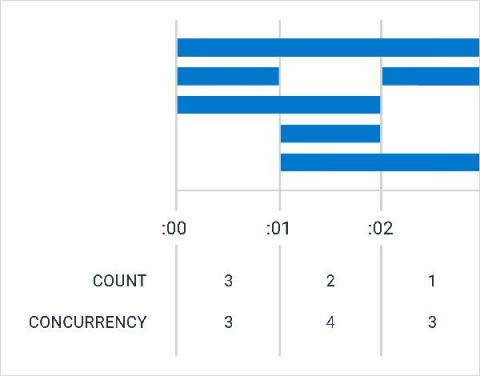
Understanding Lambda Sleep Cycles With CONCURRENCY
It started with a simple question: Why did one query take 10 seconds, while another almost identical query took 5? At Honeycomb, we use AWS Lambda to accelerate our query processing. It mostly works well, but it can be hard to understand and led us to wonder: What was really going on inside this box called Lambda? These questions kicked off the development of CONCURRENCY, a new aggregate in the Query Builder that lets us look at how many spans are active at once.
Updated: Let's Encrypt's root certificate expiry and what it means
You might have seen the name “Let’s Encrypt” across the internet for the past week and it’s because their root certificate expires on 30th September. It’s been planned for a good long while, with Let’s Encrypt providing users with updates on the expiry and new certificate since 2020.
The Complete Guide to Server Monitoring
IT structures form the backbone of many companies in today's world. Servers allow connected devices to share information within a network by analyzing, processing, and recording information. They store all the company's data and enable users to access their information from any computer connected to the network. It is essential to use server monitoring tools that ensure the servers keep running effectively and smoothly to prevent crashes and keep data safe.
Announcing Support for AWS Lambda Functions running on AWS Graviton2 processors
AWS Graviton2 processors use the Arm architecture to provide high-efficiency, low-cost computing. AWS already offers the ability to provision EC2 instances powered by Graviton2, and Datadog is proud to partner with them for the launch of new Graviton2 compute resources for Lambda functions. In this post, we’ll discuss how Datadog can provide deep visibility into your Lambda functions across whichever platform you’re using.
What is OpenTelemetry: A guide to understanding OpenTelemetry and the way forward
OpenTelemetry is a vendor-neutral approach that enables DevOps and developers to collect performance metrics in a standardized manner. Currently a Cloud Native Computing Foundation (CNCF) sandbox project, OpenTelemetry was conceived by merging OpenCensus, Google's open-source method of collecting metrics and traces, and OpenTracing, a vendor-neutral API to collect traces.
Log Observability and Log Analytics
Logs play a key role in understanding your system’s performance and health. Good logging practice is also vital to power an observability platform across your system. Monitoring, in general, involves the collection and analysis of logs and other system metrics. Log analysis involves deriving insights from logs, which then feeds into observability. Observability, as we’ve said before, is really the gold standard for knowing everything about your system.