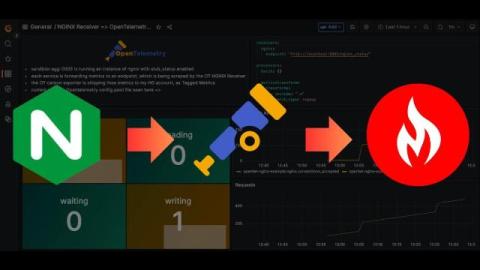
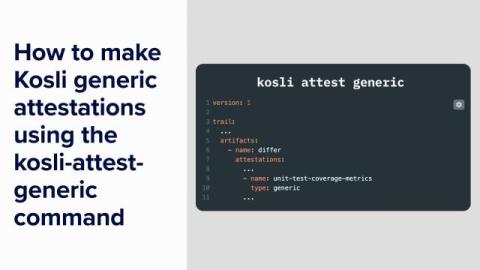
Microsoft Purview Explained
Microsoft Purview is a comprehensive solution that integrates data governance, compliance, and risk management across on-premises, multi-cloud, and SaaS environments. It is designed to help organizations classify, protect, and manage their data efficiently while maintaining regulatory compliance.